11 min read
You can now access Logs for your RPC endpoints, helping you troubleshoot issues more effectively. If you encounter an issue with your RPC calls, simply check the logs in your QuickNode dashboard to identify and resolve problems quickly. Learn more about log history limits on our pricing page.
Before you start this guide
This guide will give you an in-depth overview of crypto wallets, listing the various types of crypto wallets as well as their common security risks and threats. For an additional layer of security, we recommend using the Address Risk Scores add-on by MistTrack. With this add-on, you can easily access wallet address labels and risk scores, leveraging SlowMist’s robust Anti Money Laundering (AML) data and security expertise.
Try the Address Risk Scores Add-On by MistTrack
Overview
The attack surface for a crypto wallet is broad and many of the vulnerabilities and potential issues are often at the intersection of multiple flaws that could be present across design, security, cryptography, access, authentication, and storage. Wallet security and keeping private keys safe is the most important part of any crypto application/platform’s infrastructure. Mismanagement of private keys can be compared to handing over the keys to your safety deposit box to a bad actor.
While each independently may not cause an issue,the attack surface can increase when combined. Unlike banks and even some more centralized crypto companies, public blockchains do not have anti-fraud, customer support, or the ability to reverse transactions in the event of compromised funds.
This guide will focus on explaining the key terms for wallet security and the threats and risks of crypto wallets for both end users and builders.
Wallet Security Key Terms & Concepts
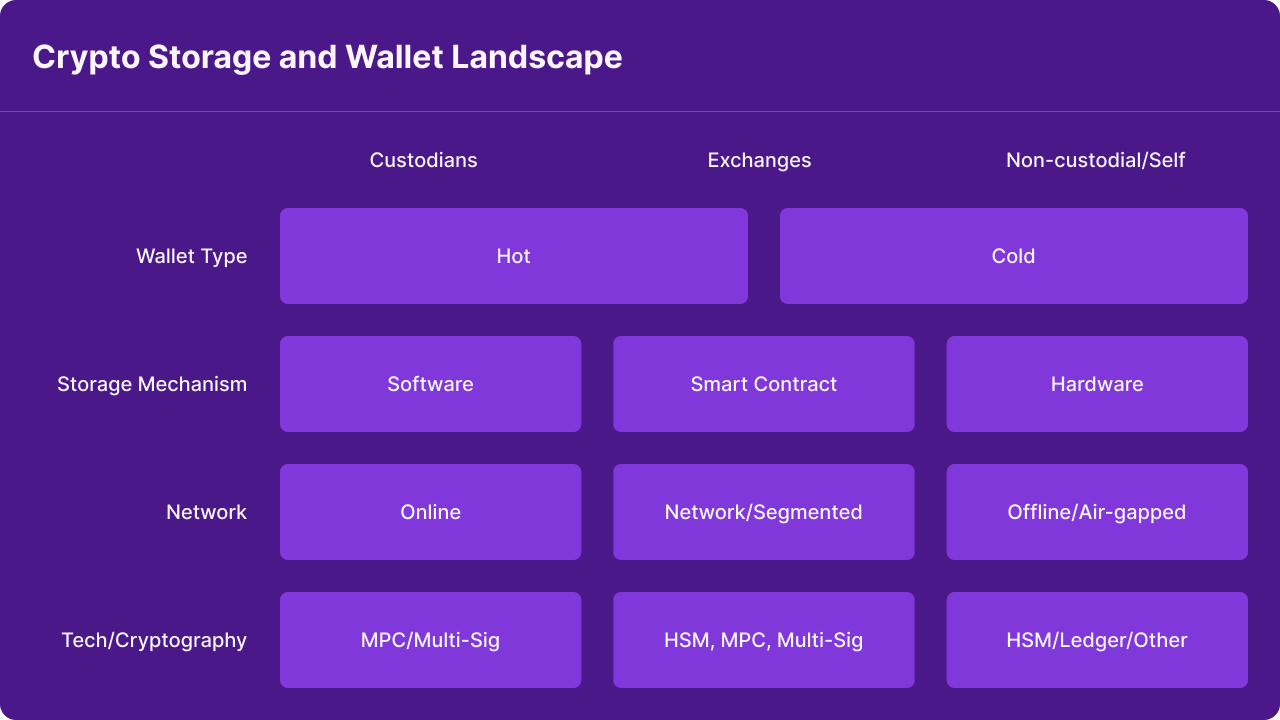
Wallet Types (Hot vs Cold, Custodial vs Non Custodial)
A crypto wallet is used to sign transactions and store the private keys that are used to interact with the blockchain network. A wallet contains a public key(the wallet address) and a private key needed to complete and sign transactions. Control of the private key means control of the assets.
There are multiple types of crypto wallets that individuals and organizations can utilize. The level of security is different per wallet type. Depending on your asset storage needs, you may use one or multiple types:
- Custodial - a third party such as an exchange or custodian is responsible for the account/wallet private keys, assets, and overall security and functionality.
Examples: Coinbase, BlockFi, Gemini
- Non Custodial - wallets that are fully controlled by the user (whether an end user or institutional user) making the user responsible for the security of the wallet, private keys, and assets stored in the wallet.
Examples: Fireblocks, DAOs, Gnosis Safe
- Hot Wallet - networked or connected to the internet in some way (mobile, web)
*Examples: Coinbase Wallet, Metamask, Phantom*
- Cold Wallet - offline, hardware, or paper, not connected to the internet in any way and usually air gapped.
Examples: Ledger, Trezor
- Smart Contract Wallet - these wallets are accessed and controlled via smart contract code and two types are supported; externally owned accounts that are accessed via a private key or seed phrase and contract accounts that are controlled via smart contract. These are more similar to a traditional finance app and include features such as; multi-signature authorization, account freezing, transaction limits, 2FA, allow listing, and guardians.
Examples: Argent, Gnosis safe
It is important to note that while exchange wallets are considered hot wallets, they are custodial and fully controlled by a third party meaning all of the key management and wallet security is handled by the custodian.
Seed Phrases & Private Keys
Seed phrases and private keys are critical parts of any wallet regardless of who it is controlled by. Both seed phrases and private keys are access keys to your cryptocurrency wallets and accounts. These are what authorize a user to access the wallet. While similar, seed phrases and private keys are also different and not interchangeable.
-
Private Key - This is your access key translated into a hex value. This is your access key to the given underlying asset address (ex: bitcoin). The address is an account where a given asset is stored. In order to gain full access to the asset address, you will need the correct private key.
-
Seed Phrase - Derived in 2013, this was invented as a way to translate access keys into words and the mnemonic phrase was born. A seed phrase is a master access key to your cryptocurrency wallet. Seed phrases also serve as a backup of your wallet. The seed phrase represents both access key and instruction for the wallet on how and which accounts to set up.
Your seed phrases and private keys should always be backed up and stored offline. Digital copies are susceptible to the vast digital threat landscape.These should be non digital copies such as pen and paper or crypto steels. Crypto steels are stainless steel units that you can use to store your seed phrases and are the metal version of a paper wallet. These simple metallic plates are waterproof, tamperproof, and fireproof. There are multiple variations of crypto steels as well as different brands however, fundamentally they all accomplish the goal of storing your private keys, and seed phrases offline safely.
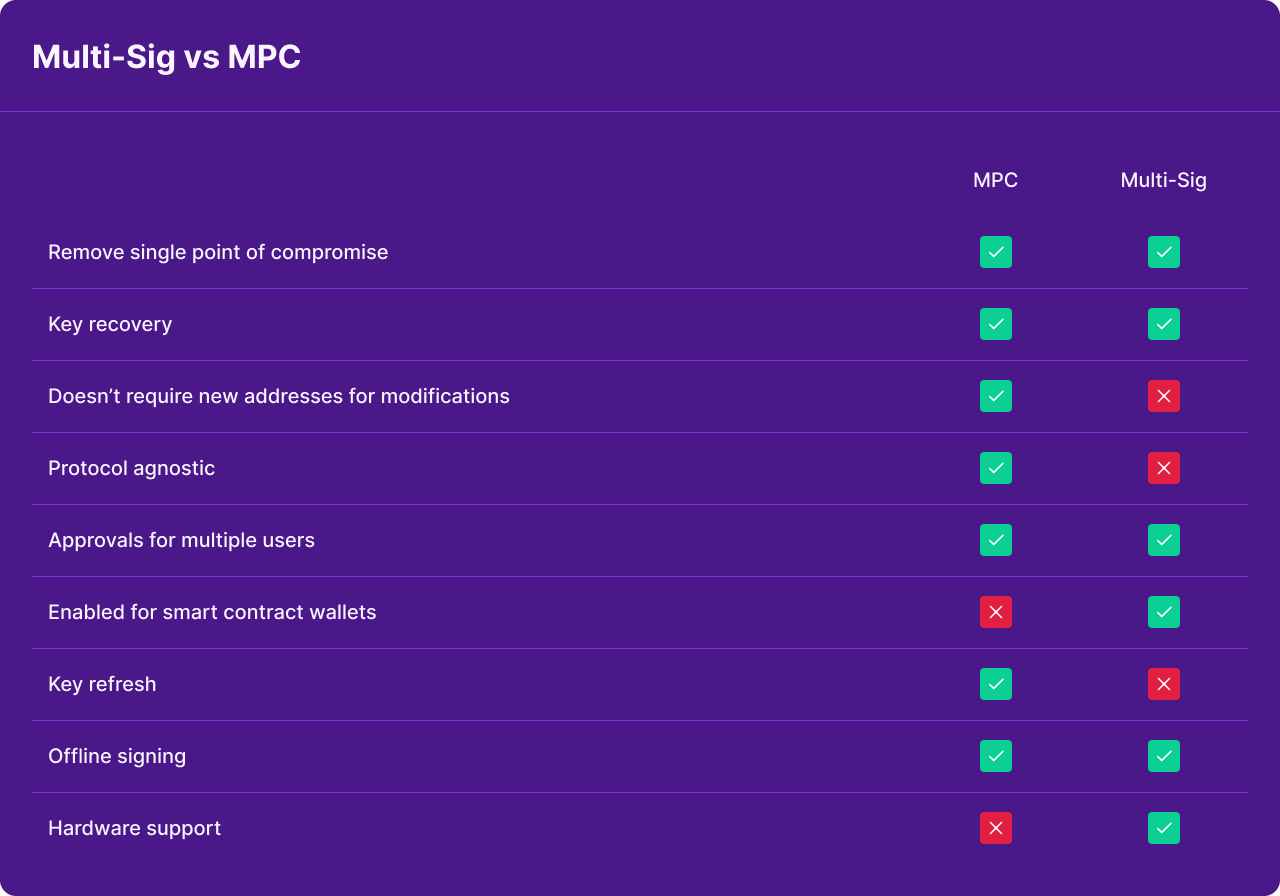
Multi-Party Computation vs Multi-Signature
Digital signature schemes are an important component of wallet security. Digital signatures are a fundamental component of blockchain technology and the primary use is to authenticate transactions. Most crypto wallets utilize either Multi-Party Computation (MPC) or Multi-Signature (Multi-Sig) as the digital signature schemes. MPC vs Multi-Sig is a long standing debate regarding which one is more secure. The reality is that there are trade offs with each and overall security comes down to the design and implementation.
-
MPC - Utilizing MPC ensures that there is no single point of failure and that a single private key is never brought together wholly during creation or in the signature. The private keys are never concentrated anywhere on a single device at any point in time and are broken up into shares, encrypted, and divided. This is done by randomizing the individual secrets. There are always more than 3 endpoints across servers or mobile devices and those secrets are never shared. The endpoints participate in a decentralized wallet creation protocol and the public key that corresponds to the set of the individual private shares (3) gets computed. Whenever a signature is requested for a tx, the quorum (of endpoints, will be 3 or more) are a part of a distributed signature process where each endpoint validates the transaction and policy and then signs the transaction.
-
Multi-Sig - Multi-Sig adds an additional layer of security to a single key that can access funds which is a historic improvement from just having a singular private key that accesses funds. Multi-Sig enables two or more people or devices to sign transactions as a group. Like MPC, Multi-Sig eliminates a single point of failure but the issues with Multi-Sig lie in interoperability and being protocol agnostic. Not all cryptocurrencies or DAOs support Multi-Sig as each protocol requires a wallet provider to implement different code. New wallets would need to be created to modify quorums and refresh any keys. This was established when it was just BTC as a currency that was around, and has posed different challenges for different protocol layers. Due to some of the limitations with Multi-Sig it can be difficult to securely support new assets and the management of multiple implementations across different chains can be difficult to stay on top of.
Wallet Vulnerabilities & Threats
Vulnerabilities and threats can be specific to crypto wallets as well as the device or operating system being used to host the wallet. True wallet security relies on a combination and integration of security across the wallet and the device or platform being used.
- Mobile app wallets - wallets that are able to be stored on mobile devices are subject to mobile vulnerabilities. Many applications including crypto wallet applications do not have the ability to check if a device is trusted, rooted, jailbroken, malicious, or has harmful tools installed. Mobile malware can be used to steal users’ credentials, seed phrases, or private keys from application memory. If wallet apps do not require a device level passcode, it can be easy for attackers to unlock the device or even access keychains and key storage.
- Web/browser based wallets - web/browser based wallets have unlimited malware possibilities. Browsers are typically a target for exploits and 0days that can grant memory access to attackers. It is also common to see phishing attempts that insert a malicious version of sensitive transaction screens such as “import account” or “send transaction”. Replacing the content of the clipboard with an attacker’s wallet address is also a common attack.
- Exchange/Custodial wallets - due to their nature of being custodial and controlled entirely by a third party these wallets are subject to a wider range of threats. For example, the entire entity controlling your funds has to deploy enterprise wide security, key management, application security, data security, etc. to secure your funds and information. Users are trusting an organization to manage their wallet and data. Additionally, users that are utilizing custodial services are susceptible to phishing scams that can harvest login credentials.
- Cryptographic operations - crypto wallets perform many cryptographic operations. Some of these operations are derived from the cryptography community however, there is still room for error. Cryptographic code can suffer from design flaws and implementation mistakes and requires a very niche development skill set. Typically cryptographic issues are a combination of design implementation mistakes.
- DeFi and decentralized apps - integration with dApps is a common wallet feature. Some wallets will allow a user to interact with a pre-defined list of dApps or embed them as a web view. Wallet integrations with dApps introduce several threat vectors such as; communication between the wallet and the dApp, malicious dApps, and potential platform risks for web and mobile. Attackers can intercept and modify requests as a result of poor authentication, data-in-transit encryption, and authorization of transaction data. Even if dApps are coming from a “trusted source” they could still be malicious or compromised by a malicious actor. Most blockchains and wallets don’t have anti-spam or anti-abuse protocols so a malicious dApp could spam the wallet with fraudulent requests.
- Third party libraries and dependencies - crypto wallets often incorporate dependencies and libraries that can have access to sensitive wallet data such as private keys. If a library or dependency has a vulnerability, this can result in the entire wallet having this vulnerability or something even more serious.
Best Practices & General Security for Wallets
How Uses Can Keep Their Wallets Safe:
-
Protect your passwords by using a password manager to generate complex and unique passwords and for secure storage. If you create a strong, complex password via a password manager you typically won’t need to rotate your password too often. If you think you have been compromised it is best to update your passwords and 2FA immediately. Be mindful to never use the same password for multiple accounts, especially sensitive accounts related to banking apps, crypto, or your email.
-
Enable 2FA on all accounts.
-
Utilize a sensitive account only email address (or multiple) for sensitive accounts related to banking, crypto, or similar. This will widen your attack surface for a bad actor.
-
Protect your seed/recovery phrase offline and make more than one copy. Split the phrase in half and store it in two separate locations such as in safety deposit boxes.
-
Use a secure hardware wallet and keep it in a secure location.
-
Keep browsers/devices/OS up to date.
-
Verify sender email addresses before replying or sharing any information.
-
Enable allowlisting on all wallets and accounts.
-
Keep your seed phrase to yourself and keep it off devices.
-
Do not share or expose your private key to anyone.
-
Only buy hardware wallets from trusted vendors and directly from the vendor.
-
When buying hardware wallets online, have them shipped to an Amazon locker location (or similar). In the event that a vendor has a data breach, your home address won’t be compromised.
-
Avoid SMS authentication and use app based 2FA.
-
When connecting your wallets to dApps or other third party sites only leave your wallet connected for the duration that you are using the dApp. - Disconnect your wallet from the site as soon as you're finished using it.
-
Balance is important. One wallet should not hold all your crypto or NFTs.
-
Utilize burner wallets to connect to sites you aren’t familiar with or for minting/airdrops. You can transfer assets to a safer and more long term storage wallet post collection.
How Builders Can Create Secure Wallets:
- Understand the network/ecosystem you are working with. The risks of crypto wallets can span across blockchains, platforms, and applications. This can also be unique per crypto asset.
- Determine what type of wallet you will need for the application you are building. For asset movements that are quick, hot wallets will be best for speed but generally less secure since they are connected to the Internet. If you don’t need to process asset movements immediately, cold storage would be best for security reasons.
- Utilizing MPC or Multi-Sig is also a design choice and usually involves a trade-off between speed, cost, and security. Keep in mind that if your digital signature scheme is insecure, the wallet implementation will not be secure.
- Balance is key. Hot wallet balances should always remain at an acceptable risk level.
- If using a custodial/non-custodial solution, ensure you have a plan for backup and recovery and that you can reconstitute key shares to move assets unilaterally. Enable 2FA on all accounts, utilize strong passwords, and set up secure policies for all asset movements.
- Add friction for sensitive actions for the end user. Require a password or pin for sensitive actions such as fund movements, add hints, show warnings, etc.
- Practice Secure Software Development Lifecycle practices (SDLC). Utilize static code analysis (SAST) tools.
- Review all dependencies and libraries before incorporating them into your build.
- Perform audits and continuously audit libraries and dependencies where possible.
- Follow best cryptography practices. Do not implement your own ciphers or protocols. Use strong encryption and be careful where you store any sensitive keys such as private keys. It is best practice to keep private keys or signing keys away from the application being used to process asset movements. Utilize secure enclaves/trusted execution environments for signing and decrypting any private key material.
- Place an emphasis on security and protection against massive exploits.
- Utilize strong transport encryption for integrations and communication.
- Implement tamper protection for wallet apps and incorporate a way to alert users if the device is not trusted.
- For mobile-based wallets, require users to set a device level passcode and send reminders that it should be set up.
- Limit the wallet applications functionality on rooted or jailbroken devices.
- Be mindful of not supporting outdated OS/devices.
- Use native, secure storage to limit the lifecycle of sensitive data.
- Utilize correct crypto primitives.
- Practice strong key management.
- Practice strong memory management of secrets.
Conclusion
Wallet security is a complex topic in crypto infrastructure and wallet security and safety is essential. The crypto wallet attack surface is massive for those trying to keep assets safe, and a rich target for attackers to go after. It is important to look at the security of crypto wallets holistically as any combination of vulnerabilities, poor design, or mistakes could result in loss of funds.
We ❤️ Feedback!
Let us know if you have any feedback or requests for new topics. We'd love to hear from you.