6 min read
Overview
Blockchains have revolutionized the way transactions are tracked; however, they also pose a potential problem: the lack of privacy for users. As every transaction and wallet address is visible to anyone who inspects the chain, individuals and organizations concerned about their activities' public exposure need to find solutions. Enter ERC-5564, an Ethereum Improvement Proposal aimed at introducing a standard for private addresses (aka stealth addresses). This guide explores the fundamental concepts of stealth addresses, focusing on the framework outlined by ERC-5564. Additionally, it will provide a hands-on demonstration using Umbra Cash, showcasing a practical demonstration of using stealth addresses.
What You Will Learn
- Learn about ERC-5564: Stealth Addresses, how it's designed and can be beneficial for private transactions
- Demonstrate how to use Umbra Cash to generate stealth addresses and implement a stealth transaction transfer
What You Will Need
What is ERC-5564: Stealth Addresses?
To quickly grasp the idea of stealth addresses with ERC-5564, let's cover a hypothetical scenario involving two parties: Alice and Bob. Suppose Alice wishes to send funds to Bob discreetly, without on-chain evidence pointing directly to Bob's known address (e.g., bob.eth).
To do this with stealth addresses:
- Bob generates a stealth meta-address and shares it with Alice. This meta-address comes with a keypair (explained later) that will eventually be used by Bob to locate and access funds.
- Alice does some computation (ideally through a UI compliant to ERC-5564), which generates a stealth address for Bob based on his stealth meta-address.
- Alice can then send the funds to the stealth address for Bob. Once the funds are received, Bob can locate the funds with his keypair set generated with his stealth meta-address and have access to the funds via his private key.
- With Bob having control of the funds, he can now keep the funds in the stealth address, transfer them to another wallet (not tied to bob), or withdraw them to a fresh exchange address.
This process (if done right) would appear to look like a transaction to a random wallet, thus masking the direct link to Bob. Note that while this method effectively obscures the relationship between Alice's and Bob's addresses (unlinkable), it doesn't completely conceal the transaction trail (untraceable). Achieving untraceability typically requires more sophisticated mechanisms like fund mixing, which are beyond the scope of stealth addresses. It's also important to keep in mind that stealth addresses are a nuanced concept in blockchain and is distinct from other privacy protocols like Monero (a privacy blockchain) and Tornado.cash (a smart contract enabling untraceable transactions), which anonymize transactions by pooling funds or using other cryptographic primitives. Also, while stealth addresses can enhance privacy, users still need to take standard privacy precautions, such as avoiding direct transactions from a personal address and a stealth address (otherwise, it defeats the purpose of using stealth addresses).
What is a Stealth meta-address?
A stealth meta-address is essentially a composite of two pairs of keys: one for spending (controlling funds) and one for viewing. Senders use the public keys of each respective keyset to send funds to the recipient via the stealth address. The corresponding private keys of the spending and viewing keyset should be kept private by the recipient as they can be used to find and control a stealth address.
The specific length and structure of these keys can vary as ERC-5564 is designed to accommodate different cryptographic approaches, however, here is an example of how a stealth meta-address would look:
st:eth:0x03d8aa420cb1fa5ca86397f84b2990276b8bd0b379793a0092cd664f03c28d067a03fbd90600c993cc02635eccb9d872ff100adced6144497c7548f712b8b57a2399
The stealth meta-address 2 standard Ethereum addresses combined. The prefix st:eth represents a standard in EIP-3770.
In the context of the Alice and Bob example, the stealth meta-address above is generated by Bob and can be shared with senders (i.e., Alice) who will generate a stealth address from it.
The corresponding spending and viewing keyset could look like this:
Spending Private Key: 0x596b90994791623a08f25c2ea709ad0a35b865893e9508fb450698acd47472fa
Viewing Private Key: 0x74a08ee7e9097ee3da4124a5c340a35b9da698654bdd5b7b0135816e995aeca6
Spending Public Key: 0x02f3309b76677ea657f82a93414e3a23e76c156148d6586c62c415968e4bda1008
Viewing Public Key: 0x0237e3c2166535144583fe86737a8d652051485cee656d813ac3fad1e0f7bde8dd
In the context of Alice and Bob, the keypair set above is generated alongside the stealth meta-address. The private keypair set should be kept secret by Bob and will be used to locate and take control of funds from a stealth address. The public spending and viewing keys are both part of the stealth meta-address (both keys combined make up the stealth meta-address).
You can generate your own addresses here for testing purposes.
Use Cases for Stealth Addresses
As discussed, stealth addresses aren't as private as other complex privacy protocols like Monero and Tornado.cash, which provide both untraceability and unlinkability, but they can still be beneficial in use cases, such as:
- Multisigs (protect the anonymity of signers on a multi-sig)
- Donations (protect the sender or recipient of transactions)
- Private investments (protect or shield an investor/trade from being disclosed)
- Payroll (protect your earnings from being disclosed)
What Standard does ERC-5564 implement?
ERC-5564 sets a standard for the generation and interaction of stealth addresses. This standardization enables users to generate stealth addresses and allows recipients to effectively locate their stealth addresses via parsing, mitigating the need to navigate various cryptographic methods for address derivation. The standard also implements for the adoption of different cryptographic schemes such as:
- Elliptic Curve Pairings
- Secp256k1
- Secp256r1
- Lattice-based
The full smart contract for ERC-5564 can be found here.
Stealth Meta-Address Registry
In conjunction with ERC-5564, there is another Ethereum Improvement Proposal: ERC-6538: Stealth Meta-Address Registry, which focuses on establishing a standardized "Registry" Contract, acting as a hub for users to store and publish their stealth meta-addresses. The registry aims to facilitate smart contract access to these meta-addresses in a programmatic manner. ERC-5564 aims to work in conjunction with ERC-6538 to allow for a complete composable smart contract framework for stealth addresses.
Stealth Addresses with Umbra Cash
Before getting started, we recommend creating an RPC endpoint on Quicknode so that you have an optimized and secure RPC communicate with the blockchain, compared to a public endpoint that may be rate limiting you or sharing your data. Create a free endpoint here and add the RPC URL to the wallet (e.g., MetaMask) you will be using to create stealth addresses.
To demonstrate stealth addresses on Ethereum, we'll show you how to use Umbra Cash. Note that Umbra uses a slightly different mechanism to generate stealth addresses compared to the one specified in the secp256k1 implementation in ERC-5564; however, it is a good way to showcase stealth addresses.
You'll need some Ether on mainnet (or any of their supported chains), and two wallet addresses (to simulate a stealth transaction). To benefit from the unlinkability stealth addresses enables, you should use wallets that don't have a history tied with each other.
Step 1. Setup Receiver Address: We'll need to set up a receiver address, which essentially creates a stealth meta-address for the recipient. First, navigate to the Setup page. You'll need to connect your wallet, sign a message (which creates an Umbra-specific pair of private keys), and finally submit a transaction to submit your corresponding public keys on-chain that users can send stealth payments to.
Step 2. Send Funds: Next, navigate to the Send page. Since we're simulating a stealth transfer, you'll need to disconnect the wallet you used for setting up your stealth address and connect a different wallet not tied to your receiver wallet in any way. This would be the recipient's personal address (e.g., bob.eth). Then, input an address you are sending to, along with the token type and amount. Then, click the Send button. Alternatively, you can copy the payment link, which preloads a send page for a user based on the URL, or see your sent history.
Step 3. Receive Funds: You can navigate to the Receive page and log back in with the wallet you used to set up your stealth address. If the transaction from the previous step is confirmed, you should see a payment available similar to the one below:
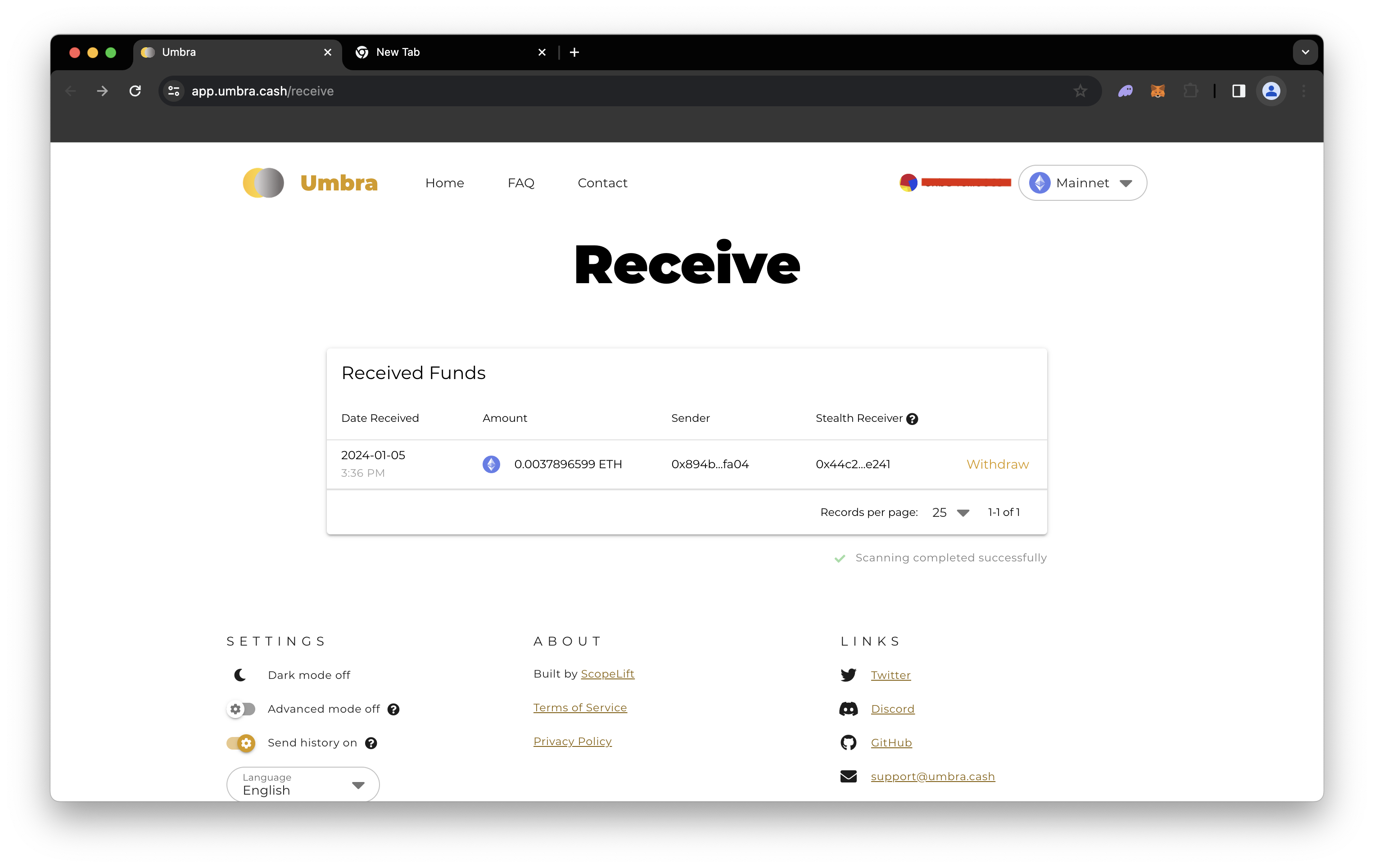
You will then be able to withdraw to any Ethereum address. This would ideally be a new centralized exchange wallet or another Ethereum wallet not tied to your address used when creating the stealth address (or it defeats the purpose).
Other Web3 Privacy Protocols
Other Web3 protocols that implement stealth addresses include:
In the next section, test your knowledge by completing the quiz.
Test Your Knowledge
Final Thoughts
That's it! I hope this guide has taught you more about privacy and transactions on Ethereum!
If you have questions, check out our Discord server or provide feedback using the form below for help. Stay up to date with the latest by following us on Twitter (@Quicknode) and Telegram announcement channel.
Additional Resources
We ❤️ Feedback!
Let us know if you have any feedback or requests for new topics. We'd love to hear from you.